Gao Feng, Li Yixi, Ma Yi, Zhang Feng
Key words: network security; LTE network security domain division; EPC network security deployment; IP bearer network security deployment; LTE network boundary security deployment
1 Introduction
With the development of mobile communication technologies, the 3GPP standards organization has launched Long Term Evolution (LTE) for wireless network evolution plans and System Architecture Evolution (SAE) projects for core network evolution plans to meet high requirements. User data rate, large system capacity, seamless coverage of network evolution needs.
The change of LTE network architecture brings new opportunities for the development of mobile communications. At the same time, features such as a flat network structure and an all-IP network bring certain security threats to the LTE network.
In order to adapt to the introduction of LTE/EPC networks and solve the security problems in the construction and evolution of LTE/EPC networks, this paper starts with the characteristics of LTE network evolution and LTE network security threat analysis, and explores and proposes the security threats faced by LTE networks by analyzing the security threats. LTE network security deployment solution.
2 LTE Network Security Threat Analysis
The key features of LTE/SAE are:
(1) Fully packetized network architecture: The network is fully IP-based, with only packet domains. The voice services are provided by the packet domain in conjunction with the IMS domain, which improves network efficiency and performance.
(2) The flattening of the network architecture: The network structure tends to be simple, and the flattening of the network is achieved through the optional integration of the S-GW and the P-GW, simplifying network deployment and shortening the delay.
(3) Support multiple access technologies: Support interworking with existing 3GPP systems, support non-3GPP network access, and support user roaming and handover between 3GPP and non-3GPP networks.
(4) High rate: The peak rate can reach 100 Mbit/s downstream and 50 Mbit/s upstream.
(5) Fast deployment: Due to the simplification of the network, the network can be rapidly deployed to adapt to the trend of continuous business enrichment.
The characteristics of the LTE network structure and services are shown in Figure 1.
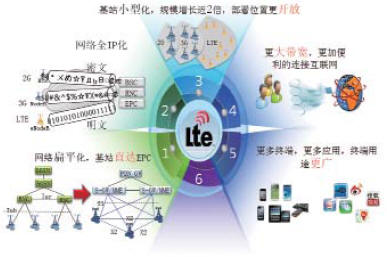
Figure 1 Characteristics of LTE network architecture and services
Due to changes in the LTE network architecture and service features, LTE networks face specific security threats, which are mainly manifested in the following aspects:
(1) Flat network structure
Without the protection of data on the backhaul network, there is a risk of data leakage; attacks from terminals and eNBs can reach EPC directly.
(2) All-IP
A connectionless and open IP network makes the attack easier; IP network security issues will be introduced into the LTE network.
(3) High bandwidth and terminal intelligence
High bandwidth makes it possible to attack mobile terminals. Mobile terminals are at risk of becoming DDoS attack tools. Terminal intelligence and application diversification make signaling storms worse, and SCTP and GTP attacks increase.
3 LTE Network Security Deployment Solution
For LTE network security threats, it is necessary to fully consider LTE network security issues and design LTE network security deployment solutions. According to the LTE network security construction requirements, an overall network security deployment plan covering the LTE network security zone division, EPC network security deployment, IP bearer network security deployment, and LTE network boundary security deployment is constructed, as shown in FIG. 2 .
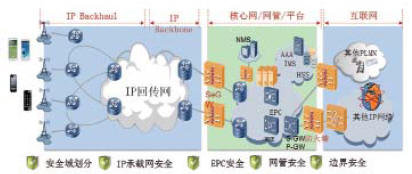
Figure 2 LTE network security deployment plan
3.1 LTE Network Security Domain
By dividing the security domain, it is possible to isolate/reduce the spread or mutual influence of security threats between security domains to some extent, thereby improving the security, reliability, and controllability of the entire network.
The principle of dividing the security domain is that the network devices that are divided into the same security domain must have the same security protection requirements, security protection levels, security access control policies, and border control policies. Each network device can trust each other.
Based on this, the LTE network can be divided into 6 security domains:
(1) E-UTRAN security domain, including eNB, PTN, CE, SEG.
(2) Core network security domains, including MME, S-GW, P-GW, BG, CE, and DNS.
(3) Accounting security domain, including CG and accounting server.
(4) User information security domain, including HSS, BOSS front-end machine.
(5) Internet security domain, including Internet access routers.
(6) OMC security domain, including LTE network management server, working terminal, security management equipment, firewall, and data communication equipment that forms the local network.
3.2 LTE Network Boundary Security
The LTE network boundary security includes three parts: security between the LTE core network and the OMC, between the LTE core network and the Internet, and between the LTE core network and other PLMNs.
(1) Between the LTE core network and OMC
The NE between the LTE core network and the OMC needs to be configured with a separate physical interface and is independent of other service traffic. To prevent attacks on the core network device, a strict authorization access mechanism needs to be configured on the OMC interface and state detection on the core network. And set the ACL packet filtering mechanism.
(2) Between the LTE core network and the Internet
Configuring firewalls, firewalls, and security policies on the borders of the LTE core network and the Internet: In the firewall security zone, configure packet filtering. It is recommended that a stateful firewall be used. In response to an external network attacking an intranet, configure security policies for typical attacks. Routing control between egress routers prevents leakage of the internal topology information of the core network.
(3) Between the LTE core network and other PLMNs
The security between the LTE core network and other PLMNs involves interfaces such as S8, S9, and S10. BGs, firewalls, and other devices are deployed at the border to control the transmission of GTP, DNS, and routing data, and to prevent security problems from other PLMNs.
Border protection strategies mainly include ACL packet filtering (available in firewalls), IP attack protection (available in firewalls), firewalls that support GTP protocol resolution, and encrypted dynamic routing protocols.
3.3 EPC Network Security
EPC network security includes business security mechanism and equipment security.
(1) Business Security Mechanism
The NAS layer, IRAT interoperable security mechanism meets the requirements of 3GPP TS 33.401. Access control: NAS signalling integrity and confidentiality protection, AKA, GUTI allocation, IMEI identification, etc.; security mechanisms in the scenario of handover between EUTRAN and EUTRAN and GERAN/UTRAN; support for UE IP address anti-piracy function (Anti- Spoofing).
(2) Equipment safety mechanism
The equipment safety mechanism covers management surface, control surface and user surface. The security protection of the management plane is mainly the secure network management connection, especially the remote connection. At the same time, it manages the user's authentication, authorization and auditing. The security protection of the control plane mainly includes the device firewall, the closing of unnecessary ports, and the opening of the security authentication of the routing protocol. The security protection of the user plane mainly uses access control lists (ACLs) to effectively limit and track attack traffic.
3.4 IP bearer network security
IP bearer network security mainly includes service access security policies and protocol protection.
(1) Service Access Security Policy
Take measures to fully ensure the security of the business system access to the IP bearer network. Services are isolated through MPLS VPNs; application systems are configured with anti-virus software; key service nodes are protected by firewalls; IP bearer networks are subject to route filtering, routing restrictions, traffic filtering, and uRPF-related security measures to control security caused by traffic impacts. Risk to ensure the safety of PE.
(2) Agreement protection measures
â—†BGP protection
Limit the legal PEER router's IP address and AS number; use the strict reverse path lookup technology on the access port to filter BGP attack packets from other network's forged source addresses. Filter ACLs on devices that cannot support strict reverse path lookup. The source address implements a similar function; a packet filtering policy is used on all Access ports to reject illegal EBGP packets.
â—†NTP protection
The IP bearer network restricts NTP packets from the external network to the bearer network through packet filtering, and performs MD5 authentication on the NTP session.
â—† Multicast protection
By default, the packet filtering technology on the access port prohibits multicast traffic, performs MD5 authentication on the MSDP, and filters SA messages on the RP.
SNMP
MD5 authentication and DES encryption are implemented, and MIB views are used to restrict access to table type variables that contain large amounts of data (routing tables and CEF tables).
3.5 Network Operation Security Management
Network operations security management covers the management and security policies of network administrators, network passwords, and network function ports.
(1) Network Administrator
Decentralizing and grading the network administrators, strictly controlling the access rights of the network, and avoiding the security risks caused by the internal administrator's misoperation. The senior network administrator can modify the configuration and delete the account; the low-level administrator can only view the network management. Interface, can not make any changes.
(2) Network password management
Implement AAA centralized management control over device access to avoid authentication of the device itself; use TACACS+ and other encrypted authentication methods to ensure that user names and passwords are encrypted on the Internet, and use One-Time passwords to prevent password forcible attacks. At the same time, the network password needs to have an audit function to prevent the password from being stolen.
(3) Network Functions and Ports
Depending on the application, disable unnecessary ports and functions (such as ICMP Redirect, Direct Broadcast, and Proxy ARP) to prevent attacks on the network system using these functions.
4 Conclusion
The change of LTE network architecture brings new opportunities for the development of mobile communications. At the same time, features such as a flat network structure and an all-IP network bring certain security threats to LTE networks. In order to adapt to the introduction of LTE/EPC networks and solve the security problems existing in the construction and evolution of LTE/EPC networks, the security threats faced by LTE networks are analyzed. Based on this, the LTE network security domain division and EPC network security deployment are proposed and constructed. The overall network security deployment plan for secure deployment of IP bearer networks and secure deployment of LTE network boundaries. The evolution of cybersecurity offensive and defensive technologies has evolved dynamically. Therefore, the deployment of network security needs continuous upgrading. With the changes in the construction and operation of LTE networks and mobile network attack technologies, new security issues may arise in the future. Therefore, it is necessary to continuously follow up and further research the network. Safe deployment plan.
Optical Prism,Dispersion Prism,Si Right Angle Prism,Chandelier Prisms
Danyang Horse Optical Co., Ltd , https://www.dyhorseoptical.com