
In recent years, the popularity of Android has been rapid, and all kinds of devices have been carrying Android systems for a long time. Mobile phones, tablets, set-top boxes, etc. have faithfully become Android users. Because Android has the highest utilization rate on mobile devices, data stored on mobile devices often involves personal privacy, such as mobile phone contacts, short message content, taking pictures, reading bibliographies, saving documents, etc., sometimes involving economic benefits. This tempts some interest groups to start making Android-based remote control programs, namely the Android Trojan.
The first Android Trojan should be Trojan-SMS.AndroidOS.FakePlayer.a, which appeared in 2010. This is a profitable Android Trojan with the purpose of deducting users' mobile phone charges. With the development of needs, purely profitable Trojans are no longer the focus. The privacy data of users is the core, especially Trojans with user behavior monitoring are the most concerned. The so-called "user behavior monitoring Trojan" means that this type of Android Trojan can monitor the user's location, said, and done.
"where" is where the user is located; "said" is the content of the call, the content of the chat; "doing" is what program is being operated and what activities are being performed.
This type of Trojan horse is often associated with the core interests of users, and often has a relatively large economic value. It is often used in private detectives, business secrets, and other areas. It is difficult to see in ordinary times, let alone understand its core code and implementation mechanism.
To this end, this article will gradually reveal to readers the core implementation technologies of these advanced Android Trojans to help everyone better understand these Trojan implementation technologies so as to protect personal privacy and prevent such Trojans from invading. The purpose of this article is to discuss the technology. Authors and magazines that use this technology to conduct illegal activities are not responsible.
| How to achieve positioning?If you use Baidu search Android positioning principle, you will find that the explanation given by Baidu is nothing more than the use of GPS or mobile base station positioning, even with Wi-Fi signals. The principle is good, but this is only the principle, but it is difficult to achieve a specific position. Taking mobile phone base station positioning as an example, the traditional implementation method is to use the API (TelephonyManager) in the Android SDK to obtain information such as MCC, MNC, LAC, and CID, then obtain the latitude and longitude of the location through Google's API, and finally obtain it through the API of GoogleMap. The actual geographical location. some of:
MCC is MobileCountryCode, mobile country code (China's 460);
MNC, MobileNetworkCode, mobile network number (China Mobile is 00, China Unicom is 01);
LAC, LocationAreaCode, location area code;
CID, CellIdentity, base station number, is a 16-bit data (range 0 to 65535).
Since Google stores information such as MCC, MNC, LAC, and CID, once we can obtain the data of the base station where the current mobile device is located, we can obtain the latitude and longitude of the base station by sending query data to Google's “http://†URL.
After getting the latitude and longitude, we convert it to the actual address. This requires sending latitude and longitude data to Google's "http://maps.google.com/maps/geo?key=abcdefg&q=" to get the actual address of the mobile device. This kind of implementation code is a lot on the Internet, you will find that they are not good, why? Because the "http://" URL is now inaccessible. This sad news made us realize that we must adopt a relatively safe method to achieve the positioning of mobile devices . In the reverse analysis of an Android Trojan horse program, a new mobile phone base station positioning and implementation technology was discovered. Of course, before this, careful readers will find out why we have been explaining in detail the positioning implementation based on mobile phone base stations instead of using the most commonly used GPS.
Since a mobile device such as a mobile phone enters a closed place such as a house, the GPS signal is attenuated to zero, which is not enough to achieve positioning, and the mobile phone signal is mostly present. Therefore, the positioning method based on the mobile phone base station is more secure, which is why Many advanced Android Trojans use this method to achieve positioning.
Closer to home, the Android Trojan that we found uses a positioning SDK based on Baidu. According to Baidu's official explanation: Baidu Android positioning SDK supports Android1.5 and above devices, providing positioning functions, through GPS, network positioning (WIFI, base station) hybrid positioning mode, return to the current location information.
Anti-geocoding function:
Analyze the coordinates of the current position and obtain detailed address description information. With such a wealth of technical support, it is no wonder that the Android Trojan uses this SDK.
The use of Baidu Android positioning SDK is very simple, first download the latest library file on Baidu's official website, copy the liblocSDK.so file to the libs/armeabi directory, copy the locSDK.jar file to the project root directory, and in the project properties - >JavaBuildPath->Libraries select AddJARs, select locSDK.jar, OK back, you can use Baidu Android positioning SDK in the program. In the code implementation, first need to initialize the LocationClient class, the code is as follows:

Then implement the BDLocationListener interface. The BDLocationListener interface has a method that receives the positioning result returned asynchronously. The parameter is a BDLocation type parameter. The code is as follows:

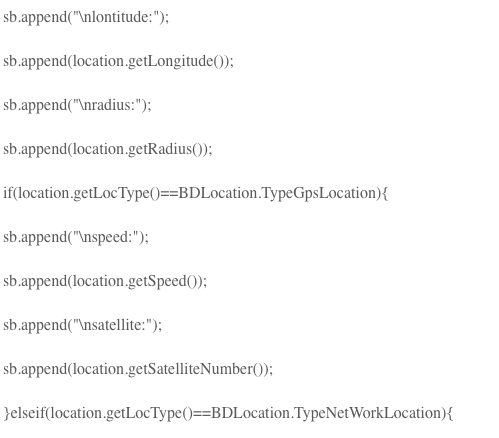
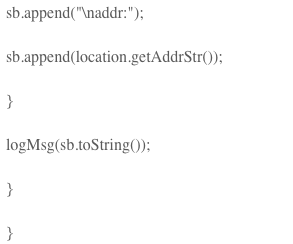
Then set the parameters. Set positioning parameters include positioning mode (single positioning, timing positioning), returning coordinate type, whether to turn on GPS, etc. The code is as follows:
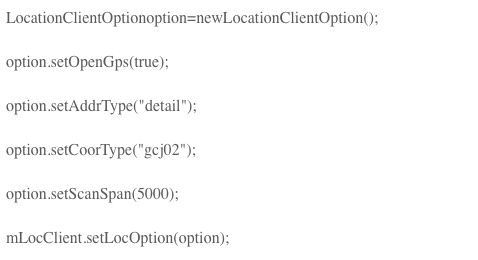
Finally, initiate a positioning request. The request process is asynchronous, and the positioning result is obtained in the above listening function. The code is as follows:
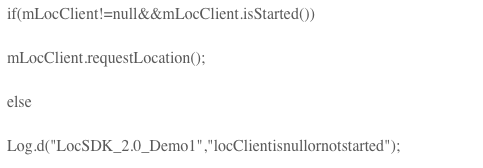
The actual test results are shown in the figure. As can be seen from the figure, the demonstration program accurately locates the location of my mobile phone at the moment and the positioning accuracy is within 100 meters. Once the Trojan horse has used such technology, it can completely monitor the user's presence. Is it a sense of horror at the moment?
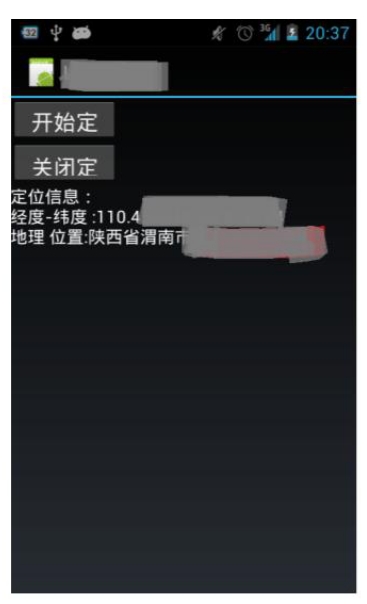
After the positioning code is implemented, the user data can be uploaded to the control site from time to time by the mobile network and can be viewed by the control end user. Combining past data, you can trace the whereabouts of a person for a period of time. For the person to be controlled, the mobile phone or other mobile device at the moment becomes the first culprit to sell himself. The successful implementation of the positioning code is only part of the advanced Android Trojan horse program, and there are many subsequent work, which will gradually reveal these core technologies to the readers one by one.
Lei Fengwang Note: This article by the FreeBuf hacker and geek (FreeBuf.COM) submission Lei Feng network (search "Lei Feng network" public concern) , the original author GDLpa, the original blog: Dangerous walk blog, reproduced must indicate the source.
Dash Cam 4K,Full Hd Dashcam,Hidden Dash Cam,Wifi Dash Cam
SHENZHEN ROSOTO TECHNOLOGY CO., LTD. , https://www.rdtkdashcam.com